
What is Strix?
Strix deploys autonomous AI agents to conduct continuous, real-world penetration tests on your systems. It proactively identifies and automatically remediates vulnerabilities, securing your infrastructure before real attackers can exploit them. Designed for security and development teams, Strix integrates seamlessly into your existing workflows to provide fast, accurate security testing without manual overhead.
Key Features
🔄 Continuous Autonomous Penetration Testing Strix agents continuously scan and simulate real-world attacks across your entire attack surface, proactively identifying vulnerabilities. This ensures your systems are always tested against the latest threats, catching issues before they become critical risks.
✅ Verified Vulnerability Exploitation Strix doesn't just scan; it actively exploits identified vulnerabilities in a controlled environment, providing live proof of impact. This dynamic testing approach significantly reduces false positives, ensuring you focus only on verified, actionable security risks.
🩹 Automated Remediation & Reporting Beyond identification, Strix generates production-ready code fixes for detected vulnerabilities. It automatically creates pull requests on GitHub, allowing for one-click remediation and streamlining your patching process.
⚙️ Developer-Centric Workflow Integration Strix seamlessly integrates with your development ecosystem, including GitHub, GitLab, Jira, and cloud platforms. Its agentic architecture provides a full hacker arsenal—from browser automation to terminal environments—empowering developers and security teams with advanced, collaborative testing tools.
Use Cases
Securing New Application Deployments: Before deploying a new web application, a development team runs Strix against their codebase and staging environment. Strix identifies an SQL injection vulnerability, validates its exploitability, and generates a pull request with a fix, preventing a critical security flaw from reaching production.
Continuous Monitoring of Existing Infrastructure: A DevOps team integrates Strix into their CI/CD pipeline for an established microservices architecture. Strix continuously tests new code changes and existing services, discovering a misconfiguration in an API endpoint that could lead to unauthorized access. It alerts the team and provides an immediate fix, maintaining an ongoing robust security posture.
Targeted Security Assessments: A cybersecurity engineer needs to specifically assess authentication and authorization flows on a critical API. They configure Strix to prioritize these areas, which then uncovers a JWT vulnerability and a privilege escalation flaw, providing detailed proof of concept and remediation steps for focused hardening.
Unique Advantages of Strix
AI-Driven Attacker Simulation: Unlike traditional tools that rely on predefined rules, Strix's AI agents emulate real attackers, dynamically exploring and testing applications. This approach uncovers complex vulnerabilities that rule-based systems often miss, providing deeper security insights.
High Fidelity, Verified Findings: Strix validates every detected vulnerability through actual exploitation, delivering live proof of impact. This significantly reduces false positives, allowing security and development teams to focus their efforts on genuine, critical issues rather than chasing misleading alerts.
Seamless Developer Workflow Integration: Strix is built for developers, offering one-click remediation through production-ready code fixes and direct pull request generation. It integrates effortlessly with your existing CI/CD pipelines, GitHub, GitLab, and project management tools, streamlining security into the development lifecycle.
Non-Destructive & Safe Exploitation: Strix employs controlled, non-destructive exploitation techniques. This ensures that while it proves vulnerabilities through real attacks, it does so without causing damage or downtime to your live production systems. All testing occurs within isolated, sandboxed Docker environments, and local processing ensures your data remains secure.
Conclusion
Strix redefines application security by bringing autonomous, AI-powered penetration testing directly into your development workflow. It empowers teams to proactively identify, validate, and remediate vulnerabilities with unparalleled efficiency and accuracy, safeguarding your systems from evolving threats.
Discover how Strix can transform your security posture and protect your systems from evolving threats.
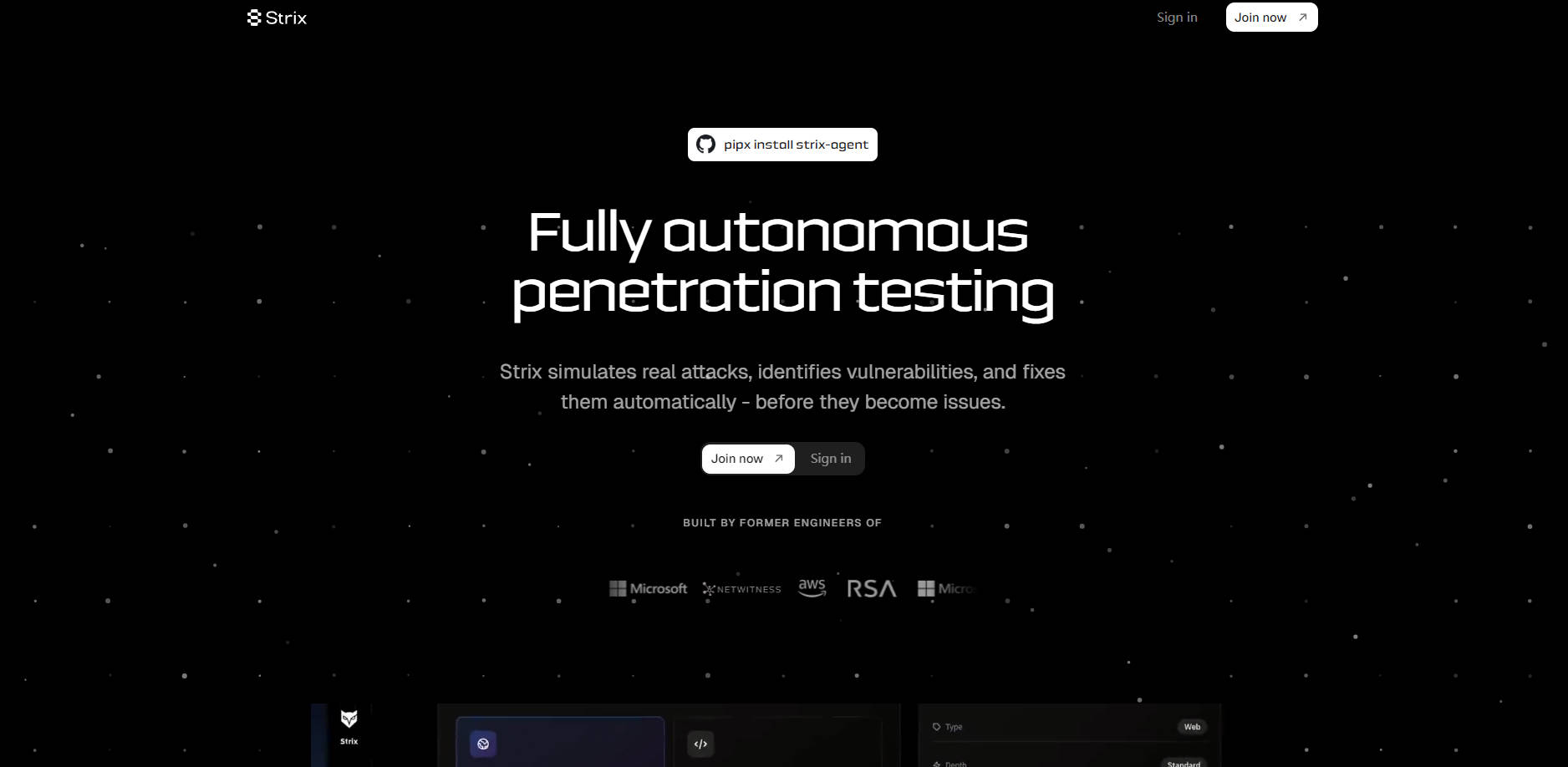
More information on Strix
Strix Alternatives
Load more Alternatives-
Astra Security: AI-powered continuous pentesting for apps, APIs & cloud. Unify DAST & expert human VAPT into agile DevSecOps for proactive, verifiable security.
-

-

-
-

Astrix automatically detects and inventories machine identities across various environments including SaaS applications, cloud infrastructures, and on-premises systems.
