What is Cloaked AI?
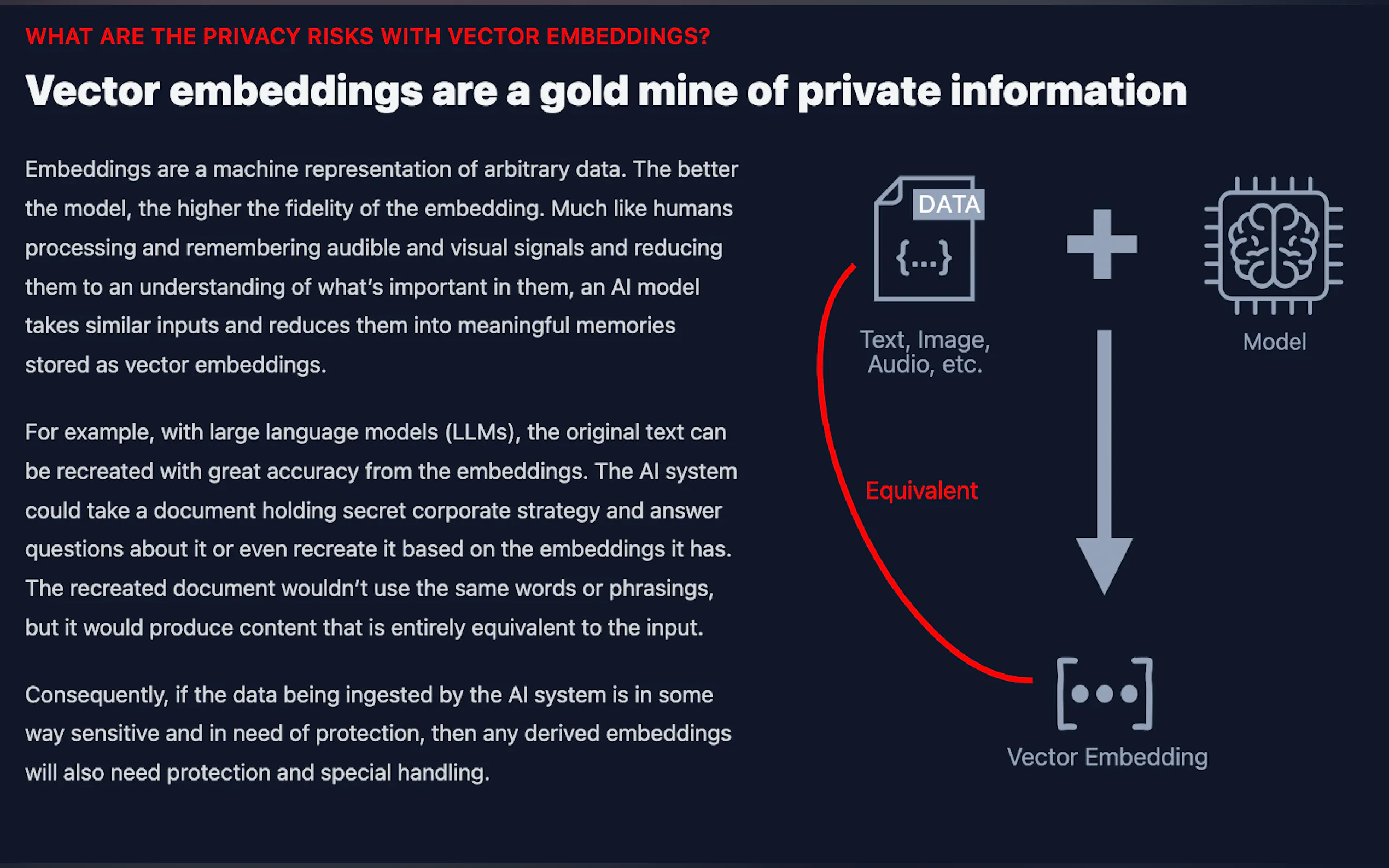
Cloaked AI offers a revolutionary solution to unleash the power of generative AI projects while safeguarding sensitive data through data-in-use encryption. By encrypting AI vector embeddings, it ensures data privacy and compliance with regulations, reducing the risk of breaches and unauthorized access.
Key Features:
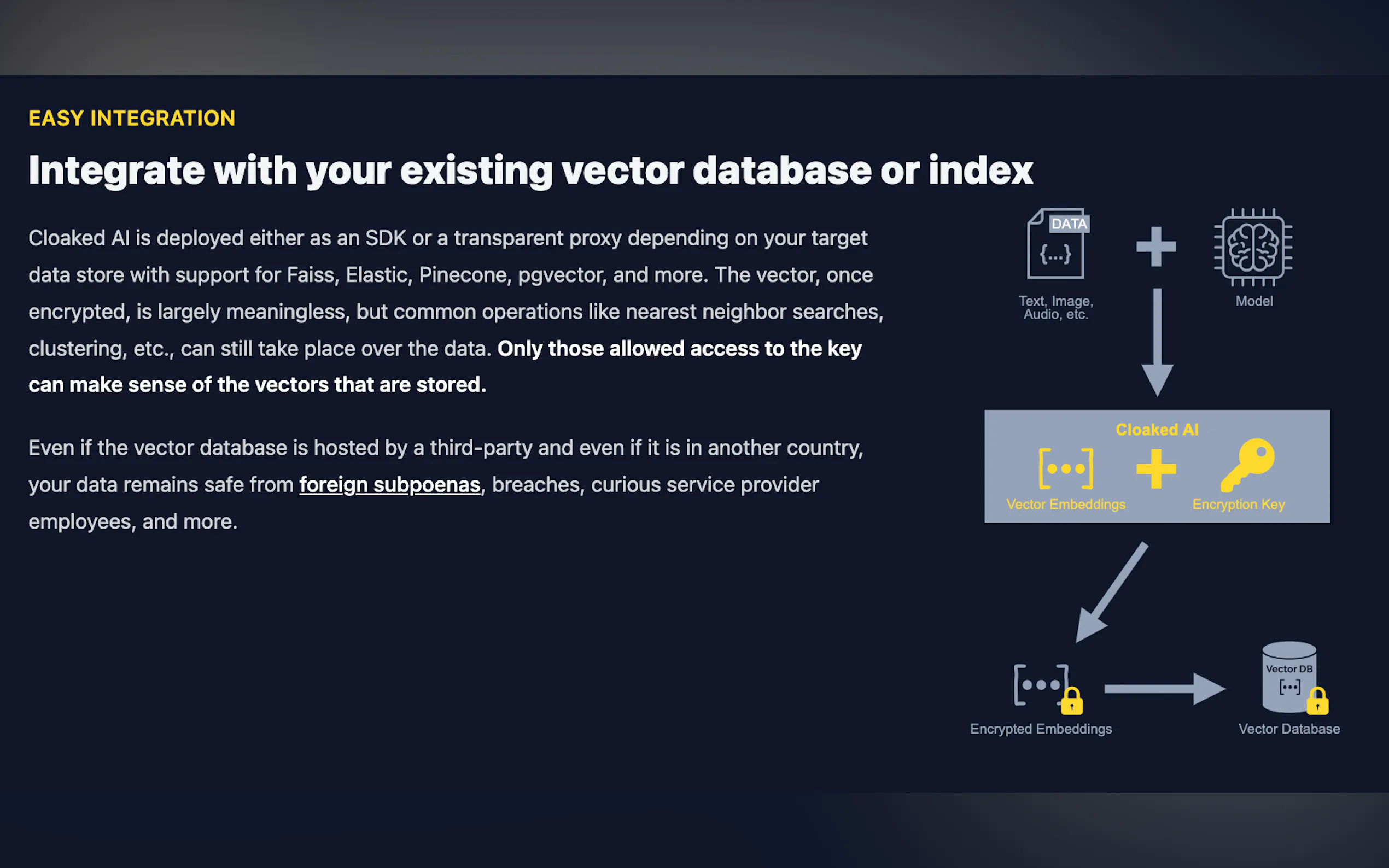
🛡️ Searchable Encryption for AI Embeddings: Cloaked AI enables encryption of AI vector embeddings while maintaining the ability to query them, reducing the risk of exposure to sensitive data.
📈 Application-layer Encryption (ALE): Protects data at the application layer, guarding against breaches, insider access, injection attacks, and cloud misconfigurations, ensuring robust security for AI workflows.
🔄 Compliance with Privacy Regulations: Facilitates compliance with privacy laws and impending AI regulations by encrypting data, enabling organizations to meet data protection obligations without compromising functionality.
Use Cases:
Recommendation Systems: Cloaked AI secures embeddings in recommendation systems, safeguarding consumer preferences and personal data against unauthorized access.
Retrieval Augmented Generation (RAG): Enables the use of private data for RAG applications, ensuring confidentiality while enhancing question/answer support over knowledge bases.
Biometric Systems: Protects biometric data such as facial recognition and voiceprints, preventing unauthorized access and ensuring privacy compliance.
Conclusion:
Cloaked AI empowers organizations to harness the full potential of AI while safeguarding sensitive data. With its seamless integration and robust encryption capabilities, it offers a secure solution for diverse applications, from recommendation systems to biometric recognition. Take the first step towards securing your AI projects with Cloaked AI and unlock the transformative power of data privacy.
FAQs:
How does Cloaked AI protect AI data?Cloaked AI utilizes data-in-use encryption, securing AI vector embeddings while allowing for query functionality, reducing the risk of data exposure.
What are the benefits of application-layer encryption (ALE)?ALE ensures robust security by encrypting data before storage, preventing unauthorized access and mitigating risks from breaches or misconfigurations.
Is Cloaked AI compatible with different AI frameworks?Yes, Cloaked AI is compatible with various frameworks like Weaviate, Elastic, Pinecone, and more, offering flexibility and ease of integration for diverse AI projects.
More information on Cloaked AI
Top 5 Countries
Traffic Sources
Cloaked AI Alternatives
Cloaked AI Alternatives-

Bearly AI: Private AI for professionals. Access GPT-4, Claude & more with zero-logging, end-to-end encryption & total data privacy. Innovate securely.
-
Deploy enterprise AI with confidence. Trylon AI prevents data leaks, blocks prompt injection, & ensures secure, compliant AI operations.
-

Privatemode AI: End-to-end encrypted AI service for secure content generation, document analysis, and automation. Protect your data with zero retention and EU compliance.
-

TrojAI provides a comprehensive AI security platform to safeguard AI models and applications against risks and threats.
-

Wald features include accessing AI assistants, sanitizing confidential data, querying internal documents securely, managing users and policies centrally, and offering "Bring your own key" data encryption.